
Access Control and Security Solutions
-
Risk Assessments and Scorecard
-
Cloud and Infrastructure Migration
-
Security System Sourcing
-
Metal Detection and Loss Prevention
-
Video Surveillance and Access management
Security
Risk
Assessments
Advanced
Detection
Technology
Access Management
Solutions
Federal guidelines
scorecard

Featured Product
CEIA USA OPENGATE®
-
Fast, Automatic & Unprecedented Screening
-
No Divesting of Luggage, Backpacks, Purses, and bags
-
Extreme Transit Flow or Throughput, with Near Zero Nuisance Alarms
-
Quick to Setup & Install – Weighs only 25 lbs. with less than 1 minute setup time
-
Ready for Anything - Indoor and Outdoor Operations
Featured Product
CEIA USA
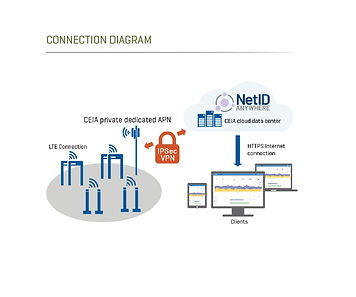
NetID Anywhere®
-
Monitor detector status and parameters
-
Avoid accidental or unwanted setting changes
-
Email notification for critical events or changes
-
Logs for every event or change in the detector
-
Advanced diagnostics capability
-
Easy third-party integration via RESTful API
Featured Products

Why Choose 415 Secure
Risk Assessment & Scorecards
We provide a risk assessment of the current access control products (detection, surveillance, and management) deployed at your facility to minimize the risk of negligent litigation using Federal guidelines and protocol.
Tailored Services
We understand that every business has unique security needs, which is why we offer customized solutions that are tailored to meet your specific requirements.
.png)
Cutting-Edge Technology
Our team of experts stays up-to-date with the latest advancements in access control and security technology to provide you with the most advanced and reliable security solutions.
Experienced Advisors
Our experienced advisors work closely with you to understand your business's security needs and provide expert guidance and support throughout the process.
Testimonials
“415 Secure provided us with a comprehensive security solution that exceeded our expectations. Their team was professional, knowledgeable, and a pleasure to work with.”

Giuliano Falcone
CISO, Traderithm.io
“415 Secure's customized security solutions have helped us protect our business and minimize risk. Their team is responsive, reliable, and always available to answer our questions.”

Frank Kobayashi
COO, Gizoom
“415 Secure's expert advisors provided us with invaluable guidance throughout the security system installation process. We highly recommend their services.”

Marvin Jacobs
CFO, IWM Holdings
Our Security Solutions in Action

Our Clients



















